ZAP Tutorial - Run ZAP on WIVET
In this tutorial, we’ll run a scan with the default zap configuration on the WIVET application to determine the crawling coverage of the ZAP scanner.
Prerequisites: Run the WIVET application (Refer to this tutorial) and configure ZAP to work with your browser (Refer to this tutorial). For this tutorial, I have configured the ZAP proxy and Firefox browser on port 8080 and I’m running the WIVET application on localhost port 8090.
The topics covered are:
- Scanner Configuration
- Run Spider
- Run AJAX Spider
- Run Active Scan
- WIVET Result
Scanner Configuration
First thing to do is to load the WIVET application on the configured browser so that the website URL appears under the Sites menu of the ZAP GUI. Next, include the website URL in the Context by right clicking on the URL > Select Include in Context > Then Select Default Context.
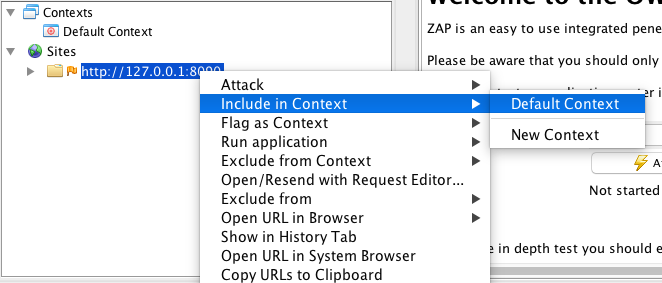
This will open up the Session Properties window and you’ll notice that the URL has been added. Before closing the window, click on the Exclude from Context option and add the following URLs using the Add button.
http://127.0.0.1:8090/offscanpages.*
http://127.0.0.1:8090/logout.php
http://127.0.0.1:8090/pages/100.php
The Session Properties window should now look like this:
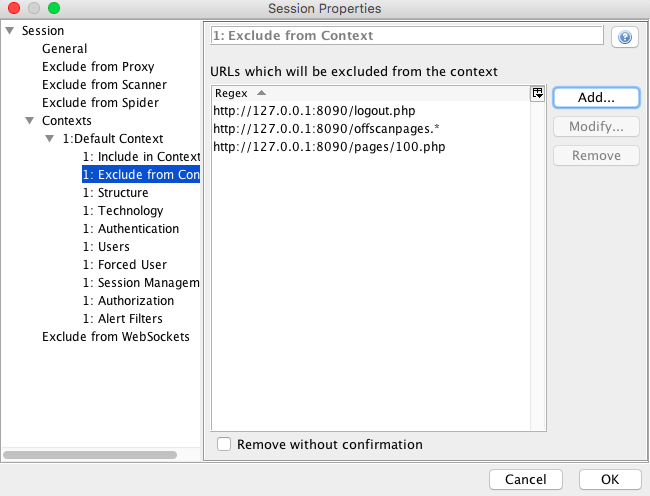
Click OK to save your changes. We added the first link so that the spider does not attack the off scan pages which are the “Statistics”, “Current Run” and “About” pages. Similarly, we added the second and third link so that the spider does not click on the logout link and logout/exit from the application before the scan is done.
The last configuration we have to do is setting the HTTP session to active. Since first we’ll run the spider, then the ajax spider and lastly the active scan, with each run a new HTTP session will be generated on the WIVET application. In order to avoid that, click on the “+” sign in the bottom tab and select HTTP Sessions.
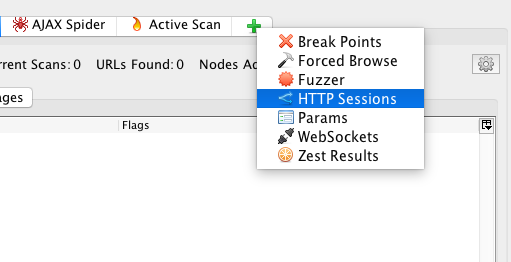
This opens up the HTTP Sessions tab on ZAP and lists the session names and values used by the application. Right click on the listed session and select Set as Active.
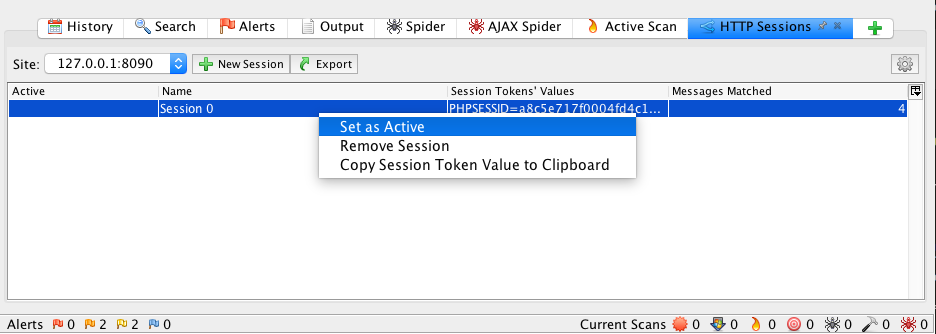
Now, you should see a green arrow under the Active column. This concludes the basic configuration that we want for this scan. What’s left to do is run a scan on the WIVET application. Using ZAP, the common practice is to first run the Spider, then run the Ajax Spider and lastly run an Active Scan. This is covered in the next few sections.
Run Spider
Under the Sites tab, right click on the website URL > Select Attack > Select Spider. In the Spider window, make sure that the Context is set to Default Context, then click Start Scan. You can view the progress of the Spider scan under the Spider tab.
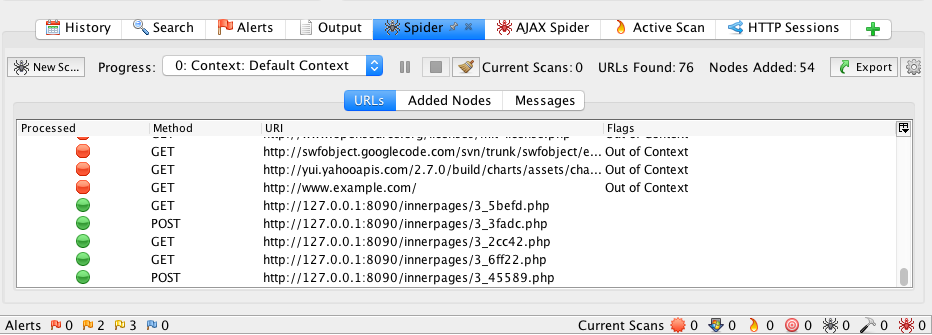
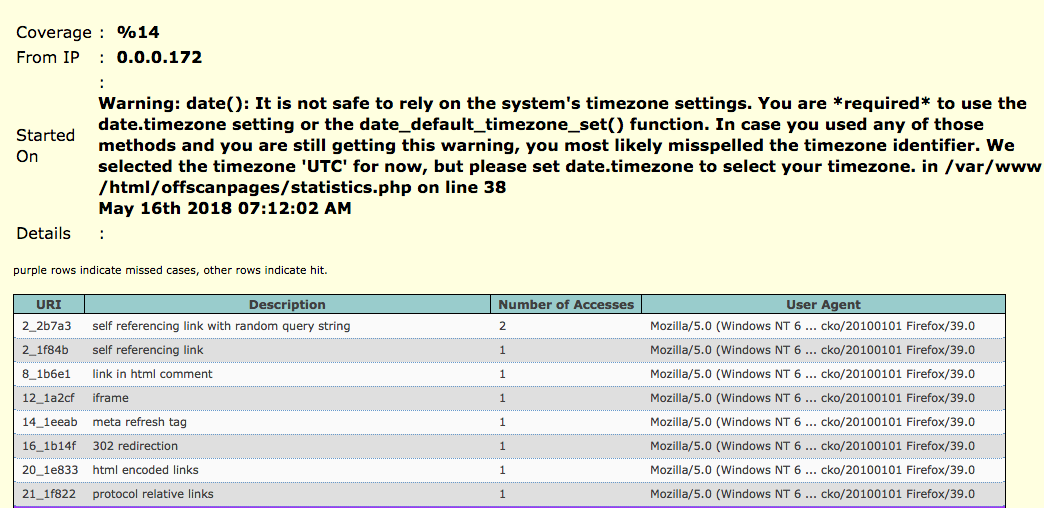
In order to view the crawling coverage in the WIVET application, click on the Current Run link on the left menu. As can be seen, the ZAP Spider acheives a score of 14%.
Run AJAX Spider
Under the Sites tab, right click on the website URL > Select Attack > Select AJAX Spider. In the AJAX Spider window, make sure that the Context is set to Default Context, then click Start Scan. You can view the progress of the AJAX Spider scan under the AJAX Spider tab.
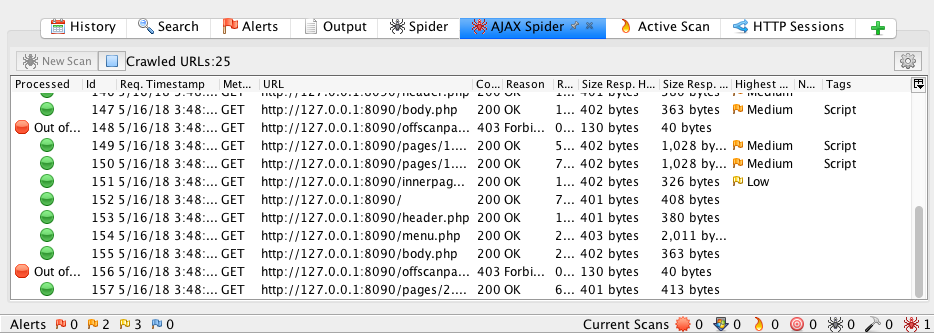
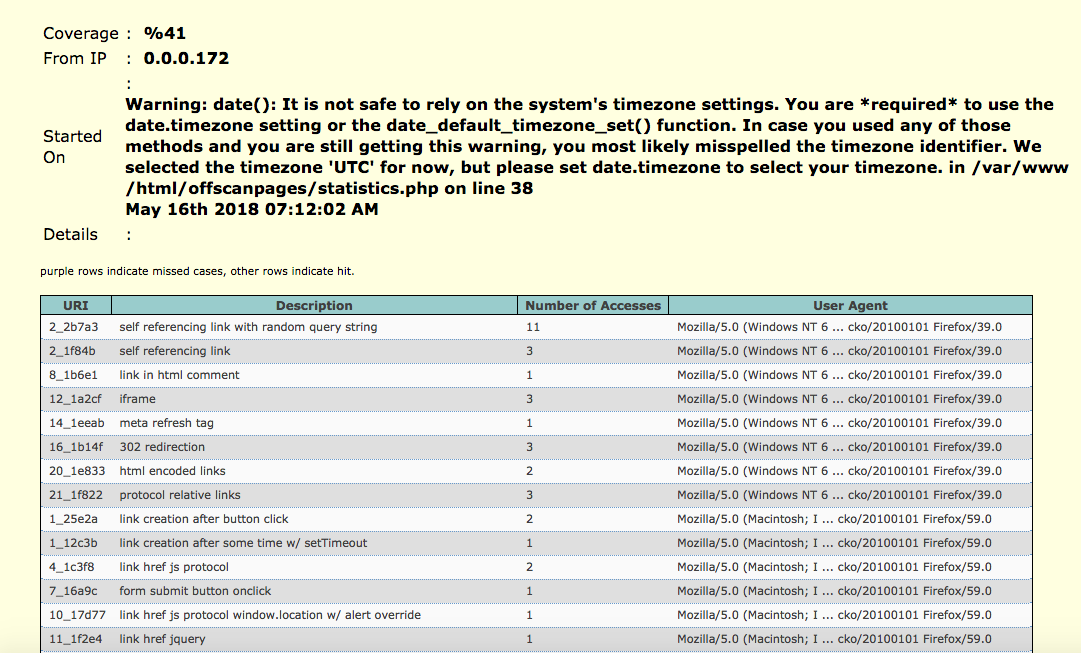
Going back to the WIVET application, you can see that the ZAP Spider and AJAX Spider acheive a score of 41%.
Run Active Scan
Under the Sites tab, right click on the website URL > Select Attack > Select Active Scan. In the Active Scan window, make sure that the Context is set to Default Context, then click Start Scan. You can view the progress of the Active Scan under the Active Scan tab.
Going back to the WIVET application, you can see that the ZAP Spider, AJAX Spider and Active Scan combined acheive a score of 42%.
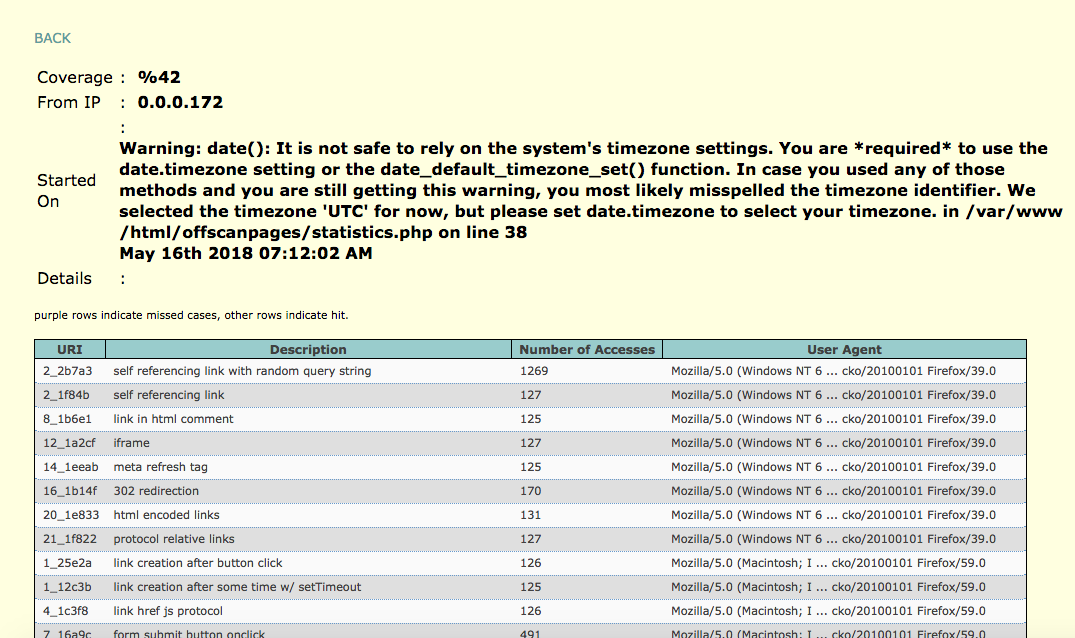
WIVET Result
As can be seen in the above sections, ZAP scores a crawling coverage of 42%, which is pretty low! One thing to note is the test was done under the default settings. If ZAP is configured properly it can acheive a score of 73%. Considering that there is a huge improvement that comes with configuration, this should shed some light on users that trust the default configuration when performing their tests. A lower crawling coverage means a lower chance of finding and exploiting vulnerabilities!